Disclaimer: This article has been written for educational purpose only. We don’t encourage hacking or cracking. In fact we are here discussing the ways that hackers are using to hack our digital assets. If we know, what methods they are using to hack, we are in very well position to secure us. It is therefore at the end of the article we also mention the prevention measures to secure us.
SS7 hacking: How hackers hack phone with ss7 to read your calls and messages
Researchers had always warned that the loopholes in SS7 are allowing hackers to steal money from banks, manipulate calls and messages. However these issues were very ignored by cellular network providers as they believed SS7 attacks are done by highly professional hackers and they require good amount of investment. However some professional hackers have proved the lack of security in cellular networks and they are successful in exploiting networks and hence leaking money from bank accounts. So, hackers can hack phone with ss7 and can read your calls and messages.
You must have seen in movies that a person wants to connect to someone and he connects to someone else. Another scenario is when the communication between two people is trapped by a third person. The third scenario is that a man in the middle manipulates the data according to him hence this is also a man in the middle attack.
These are all done by SS7 hacking. Exploiting SS7 protocols is the most common attack nowadays and thus hackers use this method to hack phone with SS7 attacks.
Signalling System 7 (SS7)
SS7 known as Signalling System 7 is a set of signalling protocols that are used for maintaining connection of calls and messages to the person you want to contact to. The main role of SS7 protocols is to make sure that the network provider knows to which sim it should send the signals. Hacking the SS7 network provides the hacker power equal to security agencies and network providers. The protocols are as old as made in 1970’s and no major changes are done till today’s date. That is why the security standards of communication are very easy to exploit because they are outdated.
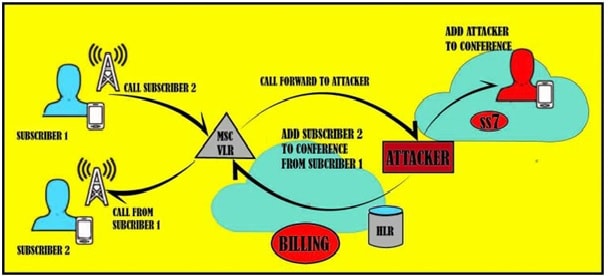
How SS7 attack is done?
The SS7 attack is done by attacking on the network provider and manipulating the signals. It is actually a man in the middle attack in which the hacker can trace your location and send signals from your phones.
Communication is not just between two people but actually the data is sent through a big chain with hundreds of links. Even if any level has weak level of security, your data can be easily hacked.
Recently it became more popular when it was found that NSA was involved in exploiting the weakness of SS7 protocols. They were able to track and trace information of millions of citizens. Those people had no idea about this until Edward Snowden opened up in the media.

How hackers use WhatsApp SS7 Hacking?

Hackers are regularly using the flaw in SS7 signalling to hack the securest platforms like Whatsapp and Telegram also. Even though they have high bits of encryption but the vulnerability lies in SS7 on which these highly used social media platforms are used.
Hackers implement Whatsapp SS7 attack by fooling the network provider that the attacker and the victim have the same phone number. When the hacker fools the telecom network he can access the complete network and hence secure platforms like Whatsapp. This is easier as it requires no need to break encryption of Whatsapp or other platforms which is very difficult but still Whatsapp ss7 hacking is quite possible with the help of tools and software.
In 2017 some hackers attacked on a German network provider and they diverted all the text messages to themselves. They manipulated the one time passwords and drained the bank accounts completely.
SS7 attacks can bypass encryption:

Everyone knows that Facebook and whatsapp use high bits of encryption. But on the other part they can be bypassed if a hacker attacks the network. In that case there is no need to decrypt the high security standards. Example: You log into facebook and click on forgot password. They directly send message to the person’s no. However by SS7 hacking one can get the messages easily hence hack into the account.
How to prevent yourself from SS7 attack?
Although the weakness in SS7 protocols is a major issue but global network telecom providers are hardly taking action. Even most of the public is unaware about SS7 hacking as mentioned by Edward Snowden. We are just made to believe that we are safe. However “No System is Safe”. So, prevent ss7 attacks or ss7 hacks with the help of above information and ethical hacking course in delhi from DICC to learn the different ways as how to prevent ss7 attacks and prevent ss7 hacks.
You can rather rely on cryptography based security verification as compared to this.







hi,
this is Jagadeesh from India
I need the software of SS7 download link on mail id
regards
Jagadeesh
send mail id ss7
I will be happy to join dicc university