Introduction: Understanding the Cybersecurity Landscape in India In today’s digital age, technology adoption among Indian businesses is on the rise. However, this surge in technology also brings with it an alarming increase in cybercrime and cyber espionage. According to Cisco’s latest cybersecurity…
read moreDisclaimer: This article is for educational purposes only and does not endorse hacking or cracking. Instead, it aims to inform the reader about the methods that hackers use to access and exploit digital assets. By understanding these tactics, individuals can better protect…
read moreDespite recent security concerns, Facebook has maintained a high level of trust among its users, who have been using the platform for many years. As a result, it is not easy to hack a Facebook account. With a continually growing user base,…
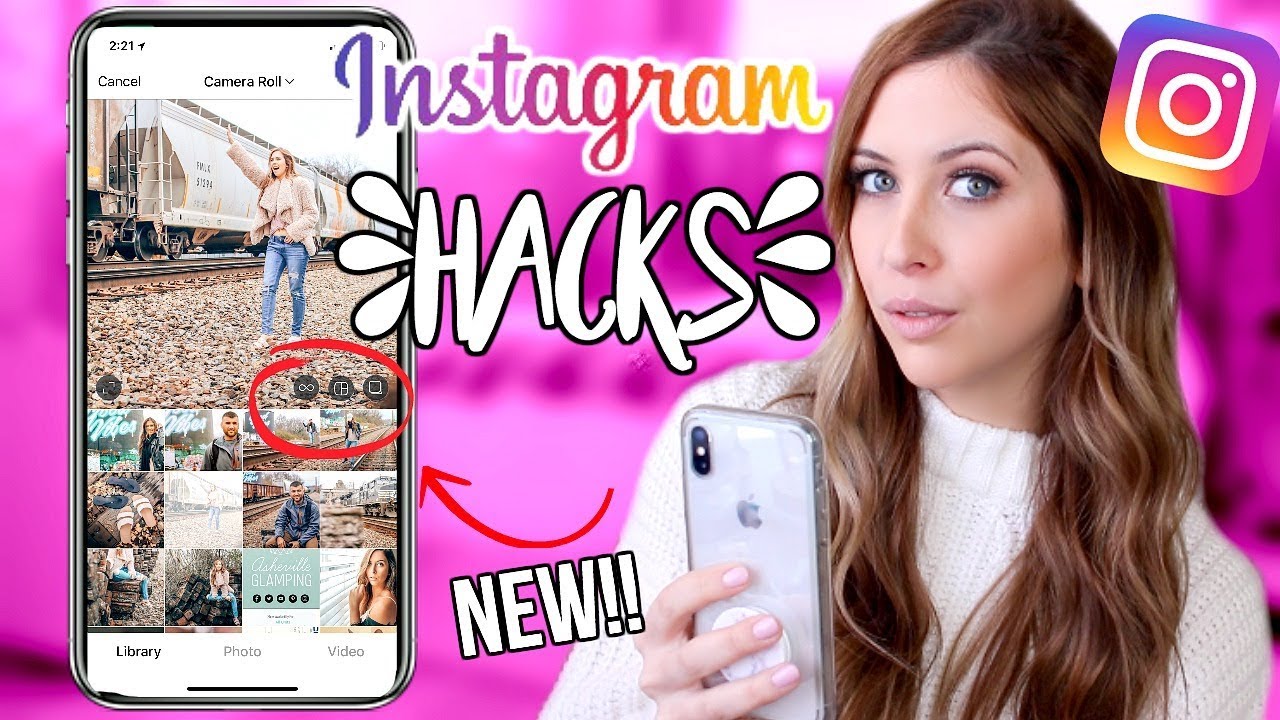
read moreDo you Want to Hack Instagram account / Instagram ID? Are you frustrated searching on the internet for How to hack Instagram ID and Password? Are You Searching For Instagram Hacker Tool 2024? Then you Have Came to Right Place, Here you Will Understand about Instagram Hacking, How to Hack Instagram Account…
read moreDisclaimer: This article has been written for educational purpose only. We don’t encourage hacking or cracking. In fact we are here discussing the ways that hackers are using to hack our digital assets. If we know, what methods they are using to…
read moreHey tech enthusiasts! We’ve got some news hot off the press, and it’s not the good kind. The Indian government, through its security arm, CERT-In, has recently issued a high-risk alert for Samsung users. So, let’s break down the jargon and understand…
read moreHumanity lives-on and extends in this digital age. Our professional, personal, and financial lives have all begun to gravitate toward the internet. Most of our time is spent on social media and other applications in our mobile phones these days. We post…
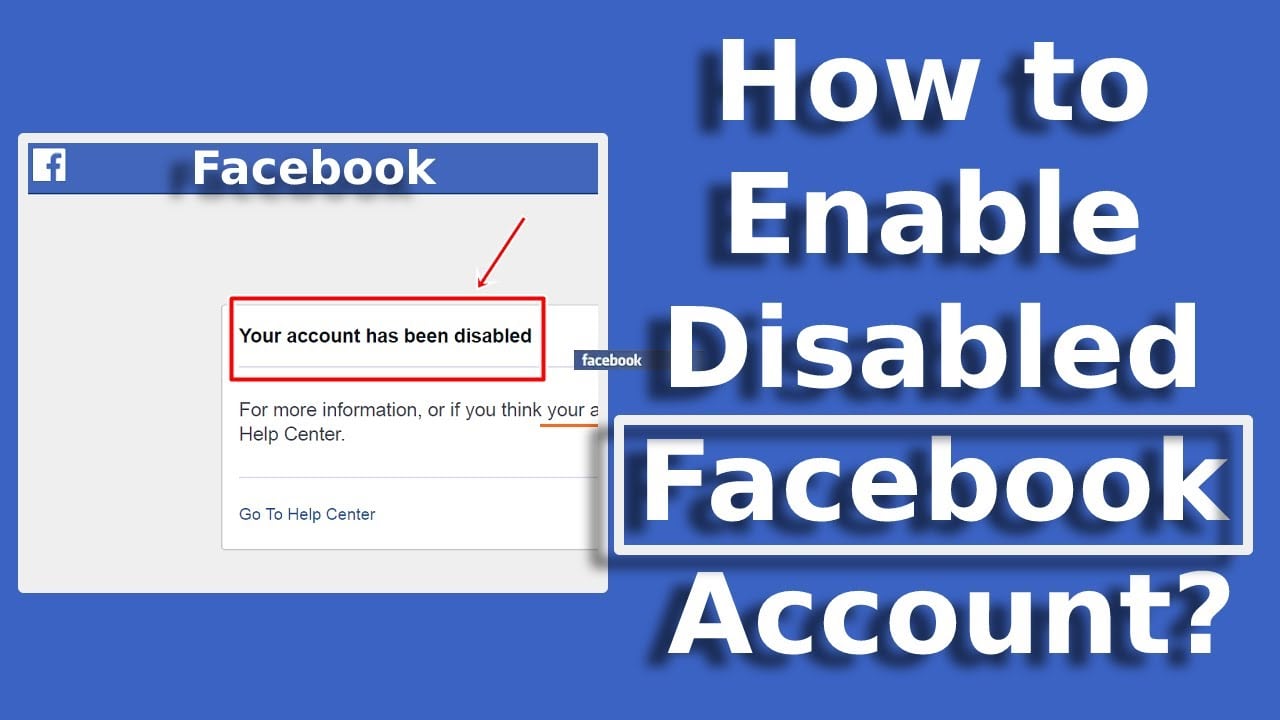
read moreDo you want to know how to get your disabled Facebook account back? You have then come to the right location. Today in this blog post, we’ll go through how to quickly and easily restore a Facebook account that has been disabled….
read moreIn our recent post, we discovered the method how we can hide our secret information behind any music media and protect it with a password. You can have a look at it Here: HIDING STUFF BEHIND ANOTHER MEDIA: MR. ROBOT But, it…
read more

![PUBG Mobile hacks Cheat Codes, PUBG Wallhack Aimbot [Proved 2024]](/blog/wp-content/uploads/2019/04/pubg-hacks-min.jpg)