Despite recent security concerns, Facebook has maintained a high level of trust among its users, who have been using the platform for many years. As a result, it is not easy to hack a Facebook account. With a continually growing user base, Facebook now boasts approximately 1.97 billion active users.
Also Read: How To Get Verified Badge On Facebook
We are very keen to Facebook and share our daily activities with our friends on Facebook. We share all the special occasions such as our birthdays, anniversaries, photos, vacations and also our businesses on Facebook. We also share the emotional moments, cherished moments and sometimes our ideology and philosophy on Facebook. We are sharing all these just to get the world aware about what we think. And hackers can easily track your activities on Facebook with the help of Facebook Tracking Tool. We strongly feel that nobody will be able to hack fb account but it’s not always true.
Also read: How to Hack Pubg and SS7 attacks to hack whatsapp
Although we may believe that the information we share on Facebook is only accessible to our friends, family, and followers, unfortunately, there are individuals with malicious intentions who can use our personal information for their own gain. These people often operate in secret and keep a close eye on our online activities, seeking opportunities to hack Facebook accounts of unsuspecting users.
Worth to Read: How to Hack Website & How to Spy on Whatsapp Messages
Also Read: How to do Wireless Wifi Hacking
Top 4 Methods to Hack Facebook Account or to Hack FB Account
You don’t need to be a professional hacker to gain access to someone’s Facebook account. With just a basic understanding of computer systems, you can learn how to hack someone’s Facebook account using proven methods. This article will provide you with some effective techniques for hacking into someone’s Facebook account. Additionally, the article will also include tips on how to prevent your own Facebook account from being hacked.
#1. Using Keylogger to hack Facebook Account:
One method for hacking into someone’s computer and obtaining their login information is through the use of a software keylogger. By downloading this software onto the victim’s PC, every keystroke they make will be recorded and sent to you via email. It’s essential that the software keylogger be installed on the victim’s computer without their knowledge, so that it can remain undetected while capturing their keystrokes in the background. Once all the data has been captured, the keylogger will then send reports of the captured information to your email.
Step by Step Guide to Use Keylogger to Hack Facebook Account
Step 1st: In the first step, download a good keylogger. You can also download emissary keylogger. You can also download some other keylogger via Google search. If you don’t have much knowledge about how to download keylogger and install in victim device, you can take help from MSPY Keylogger Phone App which can make the task easy for you. We strongly recommend it.
Step 2nd: After downloading the emissary keylogger, extract the files onto your desktop. It’s worth noting that your antivirus software may detect the keylogger and delete it, so it’s best to disable your antivirus before downloading. However, there is no need to worry about harmful viruses as the emissary keylogger does not contain any.

Step 3rd: Now, in the third step execute the emissary.exe file and you will instantly see the window as seen in the image below:
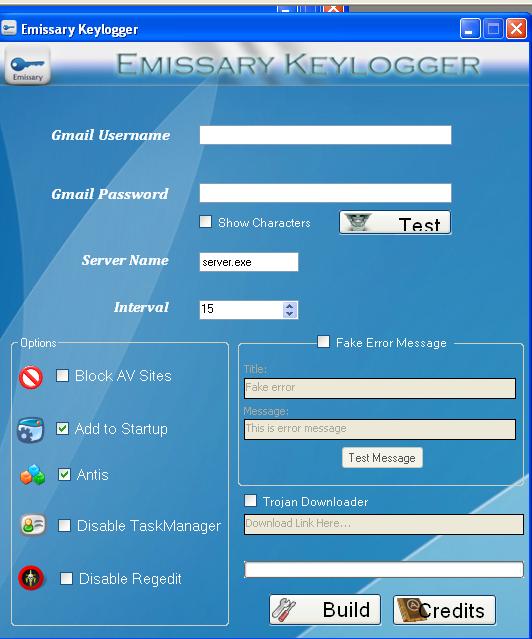
Step 4th: Moving on to the fourth step, input your Gmail account information into the keylogger and then click on “Test” to verify the connection. To ensure your privacy, you can create a fake Gmail account for this purpose. During this step, it’s important to test whether all keystroke data is being delivered to your email account as intended.
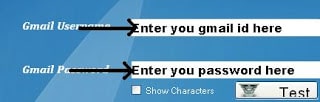
Step 5th: For the fourth step, enter the time at which you would like to receive the email reports. A recommended time interval is every 20 minutes. Additionally, it’s important to change your server file name and check all the boxes as illustrated in the image below
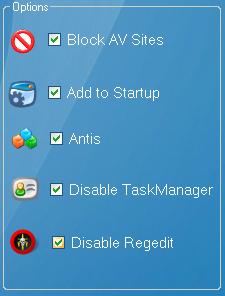
Step 6th: Now click on ‘Build’ button and create your server file (make sure that your server file is in the same directory).
Step 7th: Since this keylogger is free, it cannot be sent as a .exe file via email services. Most email services actually do not allow the sending or receiving of .exe files due to security reasons. Therefore, you will need to first encrypt and bind the file to a different type of file, such as an image, video, or document. If you’re unsure of how to encrypt and bind files, then follow the method below for binding the file:
How to Bind Keylogger with Image, PDF or any other File:
Step 1st: In the first step, you need to download any file binder. I would recommend you to download shockwaves file binder. The password is futuretricks.
Step 2nd: You would have three files now. First one is the keylogger.exe file, second one is image or pdf file in which you would like to bind keylogger and third one is shockwave file binder.
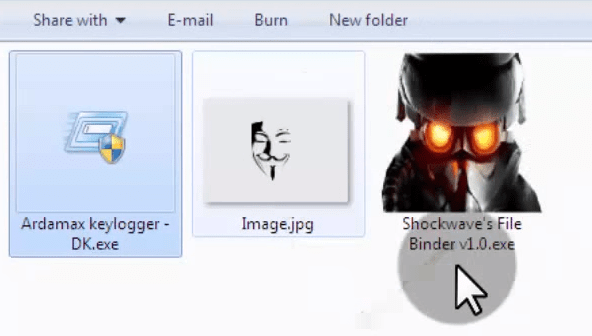
Step 3rd: Next, open the shockwave file binder, where you’ll see two browsing options. The first option is to select the image or PDF file that you want to use to bind the keylogger. The second browsing option requires you to select the keylogger .exe file, as demonstrated in the image below
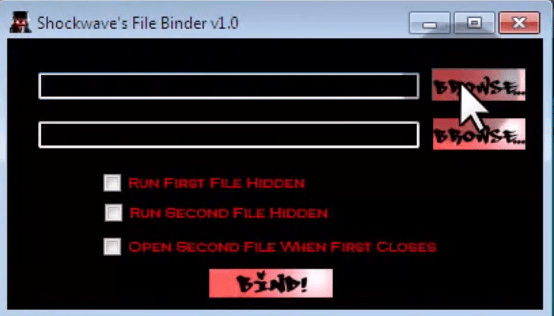
Step 4th: Now, tick on “Run Second File Hidden” and also click on Bind Button as shown in the image below:
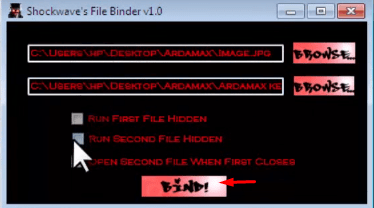
Step 5th: Now choose the name and path of the new file and your file is successfully bound with the keylogger.
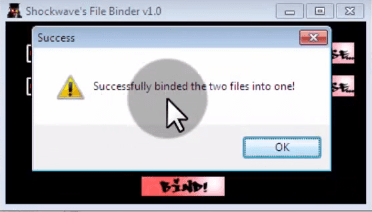
Step 6th: Now send this file to the victim and as soon as he open the image, PDF or any other file with which you had bind the keylogger, the keylogger will be installed in the victim’s computer.
Step 7th: Once the binding process is complete, you can also upload this file on free file storage websites such as mediashare, rapidshare, 4share etc. You can either send the victim the direct download link from the free storage websites.
As soon as victim execute the file you send, the keylogger file will installed on his computer and it start searches all the keystrokes including the username and passwords of facebook and send you email containing all the keylogs and screenshots from time to time as the time interval you have set earlier.
#2. Using Phishing to Hack Facebook Account
Phishing is an attack method used to hack a Facebook account by sending a fake page to the victim. When the victim enters their username and password on the fake page, the hacker can retrieve it from the page uploaded on their server.
Phishing can be carried out with or without the use of Kali Linux OS. In this article, we’ll cover both methods: creating a phishing page using Kali Linux and making a phishing page online. For the first method, you’ll need to know how to install Kali Linux on your PC.
To create a phishing page using Kali Linux OS, you can utilize the social engineering toolkit that is already installed. The phishing link should be sent to the victim from the same local area network as you, and the data that the victim enters on the fake page will be stored in a file on your machine.
Steps by Step Guide to Hack Facebook Account Using Phishing with Kali Linux
Step 1st: Open the Kali Linux with root access as ‘setoolkit’ needs you to have root access.
Step 2nd: Now Type setoolkit’ in the command line.
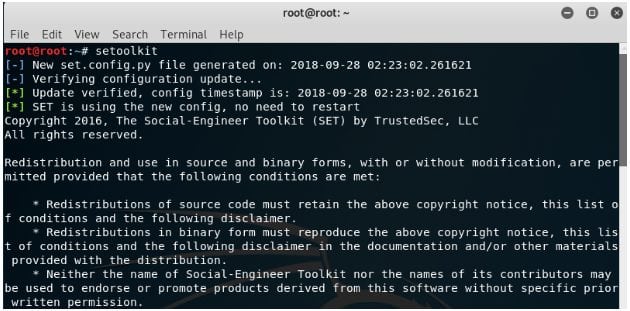
Here you will get a warning that this tool is to be used with proper license and authorization or for only educational purposes and if you use it for malicious purposes than you violate the terms and conditions of the tool.
Step 3rd: You should agree with the terms and conditions by typing Y in the command line.
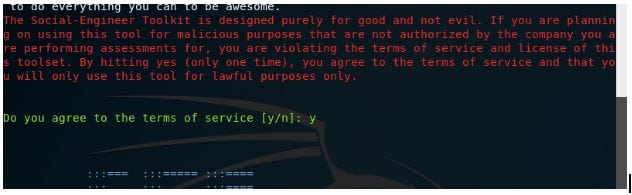
Step 4th: Here you will see a menu “next”. Enter 1 as your choice.
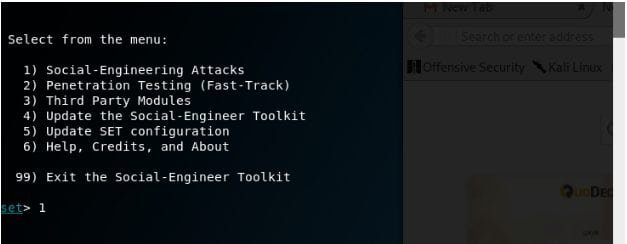
Step 5th: Enter 3 to select the ‘Credential Harvester Attack Method’ in order to get the victim’s confidential information by creating a fake page that will few form fields including the username and password options.
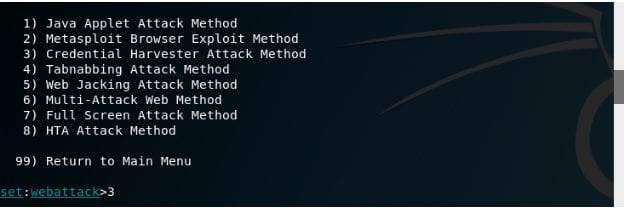
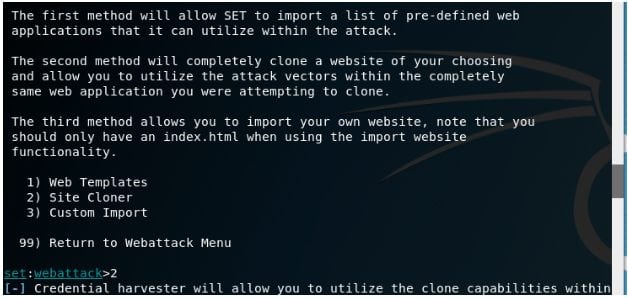
Step 6TH: Now, you do have the option here that is either to build a fraudulent page by your own or you can also clone the page of facebook site or other trustworthy site.
Step 7th: If you wish to get a Clone page than Enter 2 in the command line. It may take few minutes to create a page.
Step 8th: Now, in order to get the IP address you should open a new terminal window and write ifconfig. You should copy the IP address as mention in the “inet” field.
Step 9th: SET will ask you to put the IP address where the confidential information of the victim to be stored. Paste the IP address as you copied in the earlier step.
Step 10th: As we have chosen to make a clone of a website, we need to enter the URL or domain of the website of which we would like to make a clone.
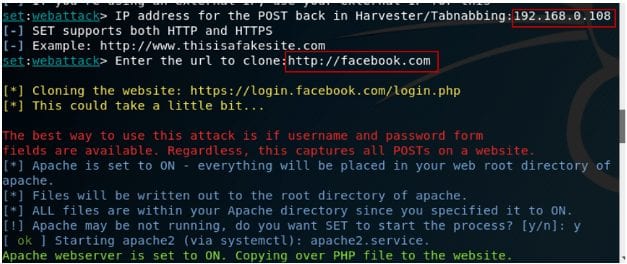
Step 11th: As the SET requires the Apache server so you should Enter Y when it prompted about starting the Apache process.
Step 12th: Till here, you have completed the setting up of Phishing page and hosted it on server. SET will make us aware about the directory at which the captured data will be stored.
Step 13th: In order to hide the IP address you should use the URL shortening services to change the URL of actual site.
Step 14th: Now Go to the browser and type http://yourIP (for example:http://192.168.0.203)
Step 15th: If the victim fills the information here in this page and clicks on “Log in”, he will be redirected to actual Facebook login page. Most often, users doesn’t take it seriously and consider it as error in Facebook.
Step 16th: In the final step you can go /var/www/html where you will be able to see the harvester file created there.
Note: The phishing method described above is intended for educational purposes only, in order to help people understand the steps that hackers may take to hack their Facebook accounts and become more aware of how to protect themselves. It is important to understand the difference between a fake page and a real one, and this can often be identified by checking the URL in the browser. It is never advisable to enter your username or password on a website whose URL you do not recognize.
Hope this step by step guide gave you a complete idea of how phishing attacks work.
#3. Hack facebook on same wifi android
This is another method using which one can hack facebook account. In this method, you can get almost 90% successes if you and the victim are on the same wifi network. I am writing this method in order to make the people aware that what hackers can do if you are on same wifi network and this is just for educational purpose so don’t use this method or any other above mentioned methods for illegal purposes.
How to Hack Facebook Account same wifi Android:
To intercept web-session profiles on different Wi-Fi networks and gain access to confidential information, including Facebook, Twitter, and Instagram usernames and passwords, you can use an Android app called Faceniff. However, this method will only work if you and the victim are on the same Wi-Fi network.
Steps to follow to hack facebook account on same WIFI
1ST Step: First, you need to install an app known as Faceniff .
2nd Step: Now, connect with the internet connection and also open the Faceniff app.
3rd Step: The next step is to click the red button. The red button you click will turn into green once the sniffer is on. It seems like that of Firesheep for android devices.
4th Step: Firesheep is an extension of firefox that enables unscrupulous users to do the same task. FaceNiff even supports WPA encrypted wireless networks.
5TH Step: In the fifth step, press the enter button and you will see the list of accounts which are connected to same WIFI network and you can choose any of the accounts.
6th Step: Now, click the account you want to hack and you will get logged in automatically and can do whatever you want with the hacked account.
How to Protect Yourself from this App: In order to protect yourself from the above attack, you need to enable HTTPS for every service wherever it is available. You should always protect your internet connection whenever you use public Wi-fi at any place such as at coffee shop, restaurants or airport with a VPN.
#4. Hack Facebook Account Using Shellphish
Requirements:
- You need to have Kali Linux operating system.
- Internet Connection
- Shell Phish (will let you know in the below steps as how to get it)
- Firefox, Chrome or any other browser.
Step by Step Guide to Hack Facebook Account with Shell Phish
Step 1: Open Fireforx with Kali linux
Step 2: Now type github.com in the browser.
Step 3: Now, you need to type shell phish in the search box available.
Step 4: Choose the first repository.
Step 5: Here you need to click on the clone or download link and copy the link
Step 6: Open the Terminal
Step 7: Now type git clone URL, and then paste the link here that you have copied before. Now, press enter.
Step 8: You will now redirected to downloading the shellphish file from here.
Step 9: Once the download complete, change your directory to shellphish by just typing “cd shellphish”.
Step 10: Now, type the commands (1s -1) within the shellphish directory. It will prompt to show you all the files and their permissions.
Step 11: Here, you will need to change the permissions of shellphish.sh
Step 12: Permissions are usually written as (-rw-r–r– ) in which (-r) means reading permissions and (w) means writing permissions.
Step 13: You will not find here the execute permissions as x. In order to add such permissions, you will require you to enter a command (chmod +x shellphish.sh). You will soon get the new permission as x just after entering the command.
Step 14: Just by typing (./shellphish.sh), you can execute the command.
Step 15: Shellphish terminal will start. From here, choose any option just by typing their numbers such as I if you want to make an instagram phishing page.
Step 16: Now, choose the port forwarding service which will provide you the phishing URL. For example, you can choose ngrok,
Step 17: If you are using it for the first time, than wait for few seconds as it will shortly start downloading ngrok.
Step 18: Once the download process is finished, it will provide you a link, which actually is the URL you can use to phish the victim.
Step 19: Now, you can easly send this lnk to your target using Whatsapp, Messanger, email or through any other media file.
Step 20: Once the target clicks over the link you send, you will instantly get its location as well as the IP address.
Step 21: Once the page open, the victim as enters the username and password in the page you given, it will be sent to you and the victim will be redirected to their instagram or facebook account whatever the phishing page is.
Top 4 Tools For Facebook Account Hacks
#1. Facebook Account Hacking with MSPY:
Facebook Messenger is a platform where a lot of private conversations take place, including those that children may not want their parents to see. To provide parents with peace of mind, there are Facebook Messenger spy apps available for installation. Despite Facebook’s efforts to improve security, it is still possible to hack into Facebook using vulnerabilities in programming languages, security loopholes, and human error. Therefore, even with advanced security measures in place, it is still possible to hack into Facebook accounts online.
Their Official Website: https://www.mspy.com/
#2. EyeZy:
EyeZy is a mobile spy application that enables parents to monitor their children’s online activities on various social media platforms. With this app, parents can protect their kids from cyberbullying and online predators. By using EyeZy, parents can easily keep track of their children’s Facebook and other social media activities, as well as keep an eye on their overall online behavior.
Official Website: https://www.eyezy.com/
FAQ About How to Hack Facebook Account
Yes, with basic computer knowledge and using certain methods like software keyloggers or phishing, it is possible to hack someone’s Facebook account.
A software keylogger is a program that records each keystroke made on a computer and sends it to a hacker’s email. It needs to be downloaded on the victim’s computer without their knowledge and remains undetectable in the background.
Yes, a free keylogger can be used, but the server .exe file needs to be crypt and bind with other files like images or documents as email services don’t allow sending or receiving .exe files.
Phishing is a method of sending a fake login page to a victim and capturing their login credentials when they enter them. The phishing link is usually sent through an email or message and appears to be a legitimate login page.
Yes, there are spy apps available that can monitor Facebook Messenger activity, including messages and other content exchanged on the platform.
While advanced security measures are in place to prevent hacking, it is still possible to hack Facebook accounts using programming language holes, security vulnerabilities, and human error. Users can take steps to protect their accounts, such as enabling two-factor authentication and avoiding suspicious links or downloads.
Conclusion:
In conclusion, the above information provides different methods and tools that can be used to hack a Facebook account. However, it is important to note that these methods should only be used for educational purposes and not for malicious intentions. It is crucial to protect your Facebook account by taking necessary measures such as using strong passwords, enabling two-factor authentication, and being cautious of suspicious links or emails. Additionally, installing spy apps can help parents monitor their children’s activities on Facebook Messenger. Overall, staying vigilant and being aware of potential security risks can go a long way in keeping your Facebook account safe.