DMARC against spam, phishing and spoofing
Spam, phishing and spoofing emails are sent out by cybercriminals in large quantities every day. Such fraudulent or falsified emails try to disguise themselves as real messages from legitimate senders and to deceive the email recipients. Manipulated e-mails with spoofed sender data or falsified content (phishing) have become a serious problem in e-mail communication because they cause great damage to recipients and compromise e-mail services and honest senders. Establishing and implementing a strict DMARC guideline helps solve this security problem.
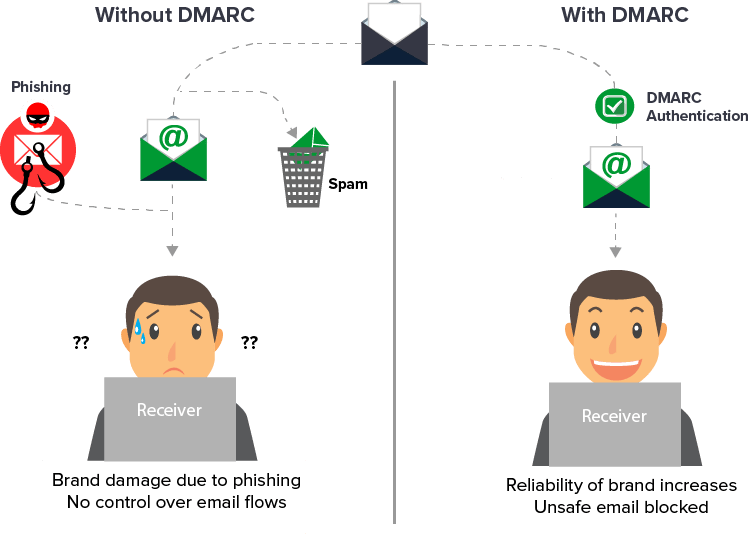
What is DMARC ?
DMARC (Domain-based Message Authentication, Reporting and Conformance; RFC 7489) is a technical standard that effectively protects email senders and recipients from phishing, spoofing and spam and effectively reduces attempts at misuse when using email.
With DMARC you can:
- define and register the email authentication methods;
- define the actions to be taken if the authentication checks of an incoming mail fail;
- enable logging, reporting and statistics on the application of the DMARC policies.
Also Read: What is VPN and how it works?
SPF, DKIM, DMARC
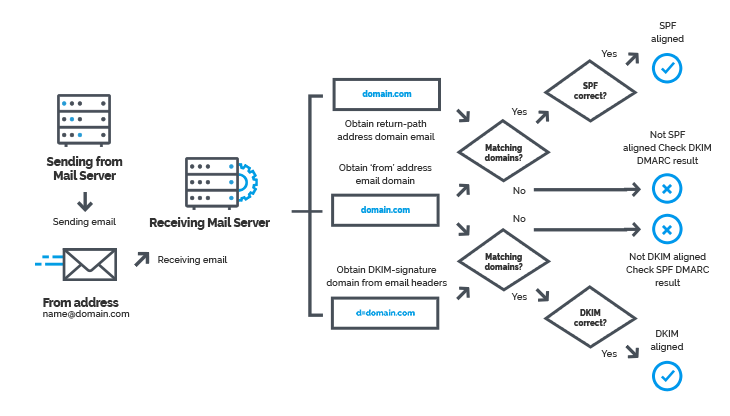
DMARC is not an independent email authentication protocol, but builds on the well-known authentication standards SPF (Sender Policy Framework; RFC 7208) and DKIM (DomainKeys Identified Mail; RFC 6376) and uses the DNS protocol. SPF records are configured using an SPF tool in public DNS.
SPF and DKIM are used in the DMARC as basic protocols for email authentication, authorization and identity verification. Based on SPF and DKIM, DMARC technology enables a recipient server to decide whether an email is delivered, moved to spam or rejected. DMARC sends summary reports to the email domain administrator about problems with message verification and delivery.
SPF, DKIM and DMARC are the three standards that work in a bundle, enable different functions of e-mail authentication and authorization and contribute to increasing e-mail security by supporting and complementing each other. Each of these standards solves its specific tasks. With SPF, senders can specify the IP addresses from which senders can send their emails for a specific recipient domain. DKIM offers an encryption process and a digital signature that verifies that incoming mail messages have not been forged or manipulated. The digital DKIM signature, similar to an S / MIME or PGP signature, ensures the integrity of the mail and the authenticity of the sender.
DMARC integrates the SPF and DKIM authentication mechanisms in a common framework and enables domain owners to declare how emails from the respective domain are treated if a security check fails.
How does DMARC work?
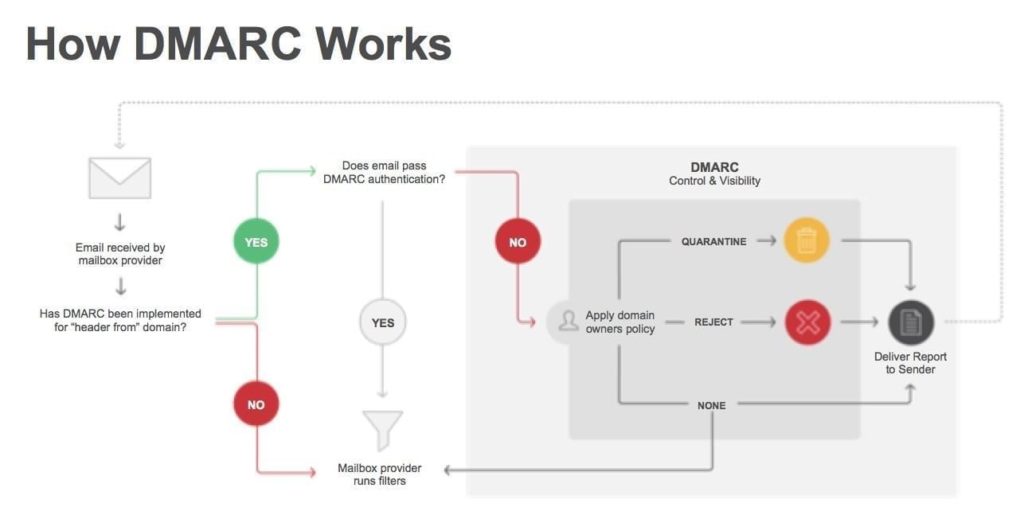
DMARC rules automatically notify domain owners of abuse of their domain. The incoming mails are checked for legitimacy and integrity using the SPF and DKIM parameters. Automatic reports with status reports, error messages and statistics are also sent to the stored email addresses. This information helps to control and improve the protective mechanisms.
DMARC does not offer new spam filters, but helps to identify and analyze the abuse. The domain owner registers a policy in the DNS that specifies what should happen to fake emails. Protection against fake emails works with DMARC in the following steps:
- The sender sends an email.
- The sender’s mail server signs the mail with DKIM.
- The mail is sent to the recipient’s mail server.
- The incoming mail is subjected to a normal security check (blacklists, rate limits, virus check, etc.) on the recipient’s mail server.
- After the standard control of the mail has been successfully completed, the mail is checked for legitimacy using the DMARC policy:
- The valid DKIM domains are extracted from the mail;
- SPF is checked;
- a suitable DMARC action is used: “Check successful” (OK) / “Spam” (a suspicious mail) / “Delete” (an incorrect or inadmissible mail).
- If the mail has passed the DMARC control, it is checked for legitimacy using other standard methods (anti-spam filter, etc.).
- The recipient receives the email.
The introduction of DMARC
DMARC requires authorization of all legitimate mail. For this not only the authorization methods SPF and DKIM have to be used, but also ensure that the authorization for all legitimate mails of the respective sender domain is carried out. Therefore, the introduction of DMARC should start with the following approach:
1. Analyze and categorize the legitimate mail traffic originating from your domain and the subdomains.
2. For each category of mail you have to implement SPF and find out the possibilities to sign mail with DKIM.
3. Implement SPF for the domain and subdomains: The sender must configure SPF data records and the public DKIM key for the considered shipping domains (DMARC Policy Domain). It is recommended to use the denial policy for domains that are particularly security-relevant. Although many recipients do not block mail at SPF, even if strict guidelines are published, they use SPF for weight classification. In practice, this is the SPF mode that is used most frequently and corresponds to the recommendations of the standard.
4. Publish a DMARC record with policy “p = none” for the primary domain and subdomains.
5. Deploy DKIM: It is recommended to use the key length of 1024 or 2048 bits. With fo = 1 in the DMARC guideline you can receive detailed reports on all problems with SPF and DKIM, also for mails that have passed the DMARC authorization.
6. Switch to a real DMARC policy: In DMARC-Policy you determine how to deal with unauthenticated mails (if the authentication check does not pass). Do not use the “quarantine” policy for a long time, as this can mask existing problems and you may only learn from aggregated reports about the problems that have occurred, which can take more than a day to receive. You can start by enabling the rejection policy by approximately 10% (p = reject; pct = 10) to track potential problems with delivery errors. However, it is not recommended to maintain such a policy for a longer period of time: the quarantine policy is applied to the remaining 90%, and individual problems can be overlooked.
7. Optimization of the DMARC guidelines: You can use the following DMARC parameters to optimize:
- p – DMARC directive;
- sp – Policy for subdomains that do not publish their own policies;
- pct – percentage of mail to which the policy applies;
- rua – the email address to which statistical reports are sent;
- call – the email address to which forensic reports are sent;
- fo – send notifications (fo = 1) or do not send (fo = 0) in the
- event of violations adkim – verification mode for domain
- conformity DKIM aspf – verification mode for domain conformity SPF
There are various tools for visualizing DMARC reports. Dmarcian offers paid and free services (for smaller amounts of e-mail) as well as a practical free XML viewer for displaying DMARC reports. Agari and Proofpoint also offer commercial services to implement and support DMARC.
Conclusion
Individuals, companies and organizations strive to filter spam, malware and phishing out of email traffic. Before DMARC, it was a difficult task to check incoming emails for authenticity and to ensure their integrity. However, if the automatic filters of the mail servers fail and real emails cannot distinguish between spam and fraud, it is up to the end user as the email recipient to reliably identify and delete such dangerous emails. Many inexperienced users open unknown e-mails to read the messages and thus take on high security risks. This is the reason why email accounts for more than 90% of all Internet attacks.
DMARC aims to provide the sending domain with aggregated and forensic feedback on the effectiveness of its email authentication strategy. The main goal of DMARC is to filter out and block falsified mails on mail servers before they reach the recipients. For email security, DMARC is a necessary safeguard, but not an easy task. Only at first glance does it seem sufficient to publish an entry in the DNS. In order to rule out misuse with regard to DMARC reporting, an authentication and verification system must be implemented in accordance with RFC 7489.
DMARC encourages senders to fully authenticate their outgoing email, making the email service work safely and reliably. DMARC is particularly effective and increases the security level of the e-mail services when DMARC is used together with other security technologies and protection mechanisms such as S / MIME, PGP / OpenPGP and TLS-based protocols (HTTPS, SMTPS, IMAPS, POP3S etc.).
