Cyber security is a term used to describe the security of electronic information and systems from unauthorized access or theft. In the United States, the federal government, businesses, and individuals all have a role to play in cyber security. The federal government…
read moreDMARC against spam, phishing and spoofing Spam, phishing and spoofing emails are sent out by cybercriminals in large quantities every day. Such fraudulent or falsified emails try to disguise themselves as real messages from legitimate senders and to deceive the email recipients. Manipulated e-mails…
read moreJust A Single Character Can Crash Any IPhone Or Mac (Crash WhatsApp, IMessage, Facebook Messenger, Outlook For IOS, And Gmail In Any IOS) When it comes to security of operating device apple reached to milestone, but you’ll be shocked to know that a simple character…
read moreMany people consider ethical hacking to be a lucrative career opportunity, and for good reason! It’s a demanding career that never gets boring, pays well, and gives you a sense of accomplishment. In this article on “Ethical Hacking Careers,” we’ll go over…
read moreCRM is actually an acronym that stands for customer relationship management. Broadly, CRM is any practice, technology, or strategy designed to help businesses improve their customer relationships. Life is getting more social and technology is no less, Customer Relationship Management (CRM) is more like…
read moreWe all know how important Netflix has become in our lives over the past few years and it would not be wrong to mention that the online streaming portal is now an integral part of our day to day activities. Netflix is…
read moreFacebook Is one of the largest social media networks in today’s world.you may think Facebook is a very huge and famous social network.How can we Hack it?In today’s world, everything is possible.Technology and as well as tricks & Hacking methods also increasing…
read moreVPN stands for Virtual Private Network. It’s an encrypted tunnel that connects your computer to the internet. This can be used to protect your personal information when you browse online or to access websites blocked in your country. There are several VPNs,…
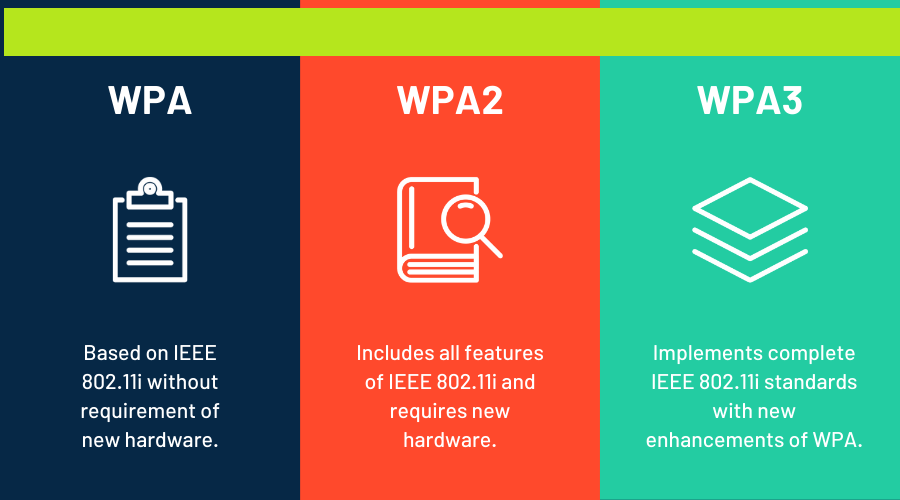
read moreToday, most users have a Wi-Fi router to connect to the Internet wirelessly from a computer as well as from mobile devices and other devices. To prevent unauthorized users from connecting wirelessly to our router, stealing our Internet connection and even accessing…
read moreHow to Backup Your Data of Computer/PC/Windows Backing up your data is very important. Indeed, even if you lose non-commercial information you will get upset. However, when it comes to data used for business, its protection is a primary concern for every…
read more